MySQL vulnerability scanner powered by Invicti DAST
Find and fix exploitable vulnerabilities in your MySQL-powered web applications—before attackers do.

G2 Awarded
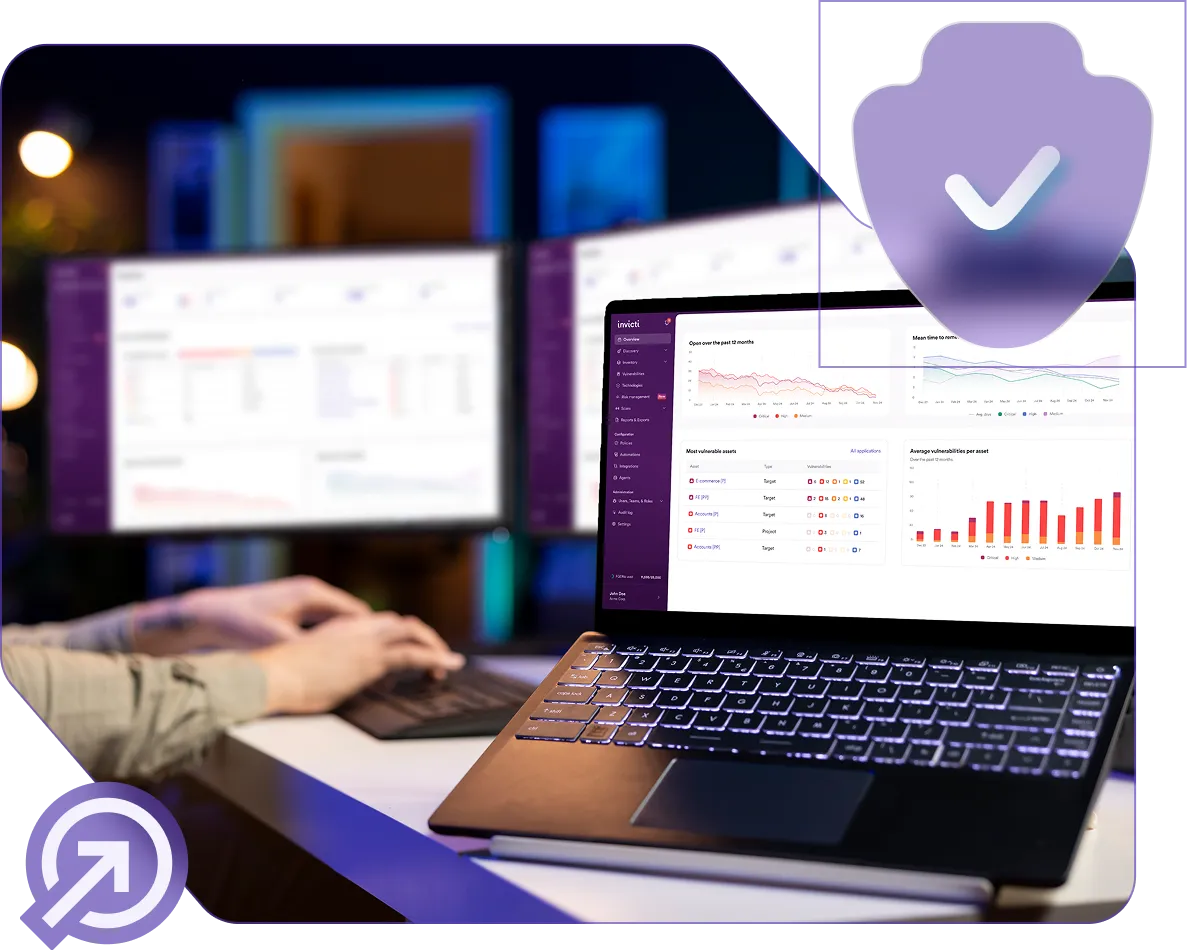
Pinpoint real risks in your MySQL stack
Invicti’s DAST-first AppSec platform can serve as a precise and efficient MySQL vulnerability scanner. By simulating real-world attacks on running web applications, DAST uncovers exploitable issues tied to your MySQL server infrastructure and application stack, including SQL injection vulnerabilities, misconfigurations, outdated components, and exposed sensitive data. This targeted capability helps organizations using MySQL, whether on Linux or Windows, eliminate guesswork and focus on risks that actually matter.
Benefits of using Invicti DAST as a MySQL scanner:
- Detects SQL injection vulnerabilities in apps and APIs backed by popular databases including MySQL and Microsoft SQL Server
- Flags outdated or vulnerable MySQL server versions
- Proves that vulnerabilities are exploitable using safe, non-destructive test payloads
- Works across all web tech stacks including PHP, open-source CMS platforms, and APIs
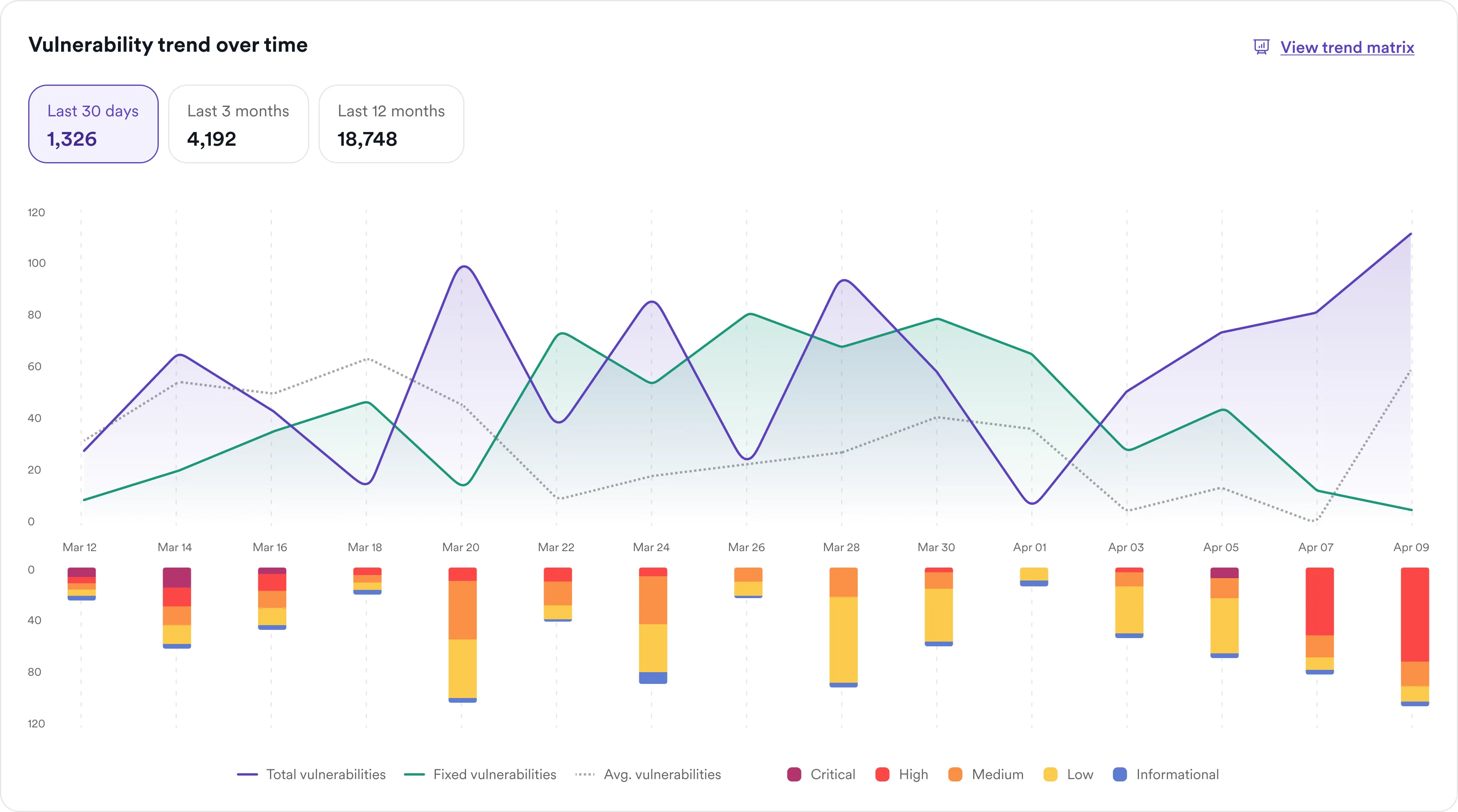
One use case—many layers of protection
Using dynamic application security testing (DAST) to scan for MySQL vulnerabilities is just a small part of its broader utility. A DAST-first approach supports application security across web servers, APIs, and databases in real time. It helps ensure that no hidden attack vector—from forgotten phpMyAdmin endpoints to brute-force authentication paths—remains untested.
Broad and deep coverage with every scan:
- Crawls web applications to uncover endpoints, parameters, and exposed SQL commands
- Covers both front-end and back-end layers, including API traffic paths
- Maps out your realistic attack surface for complete vulnerability assessment
- Flags vulnerabilities corresponding to OWASP Top 10 risks, including SQLi and authentication flaws
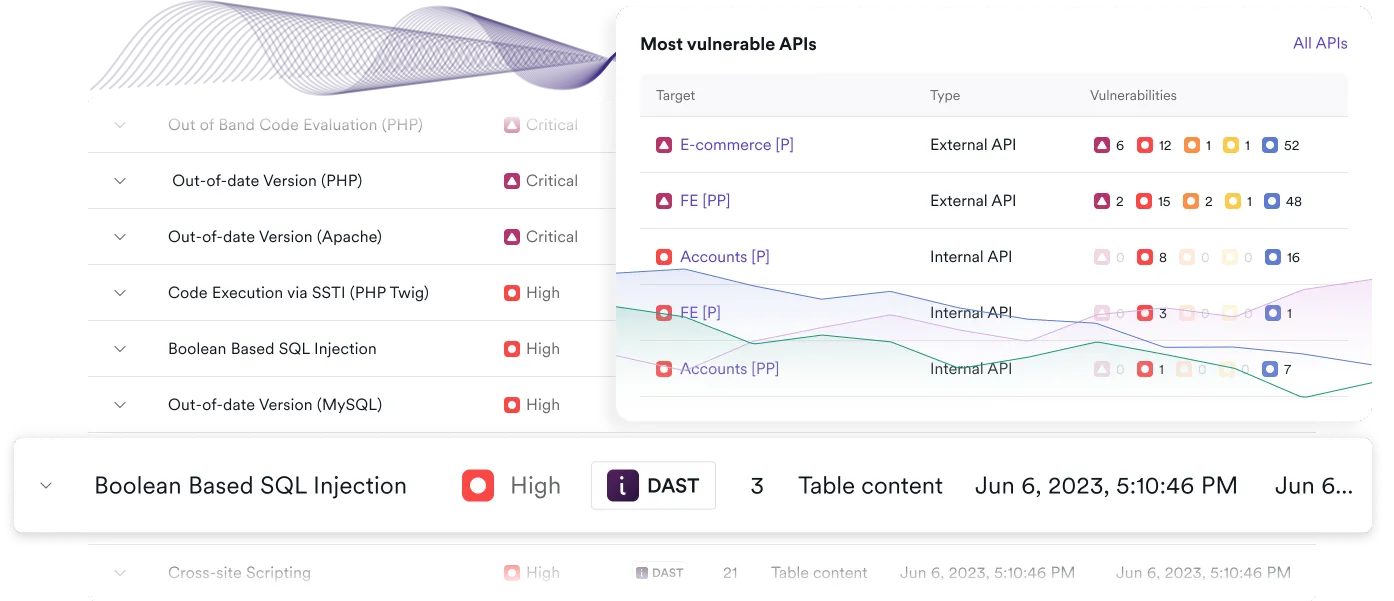
Actionable insights, not false positives
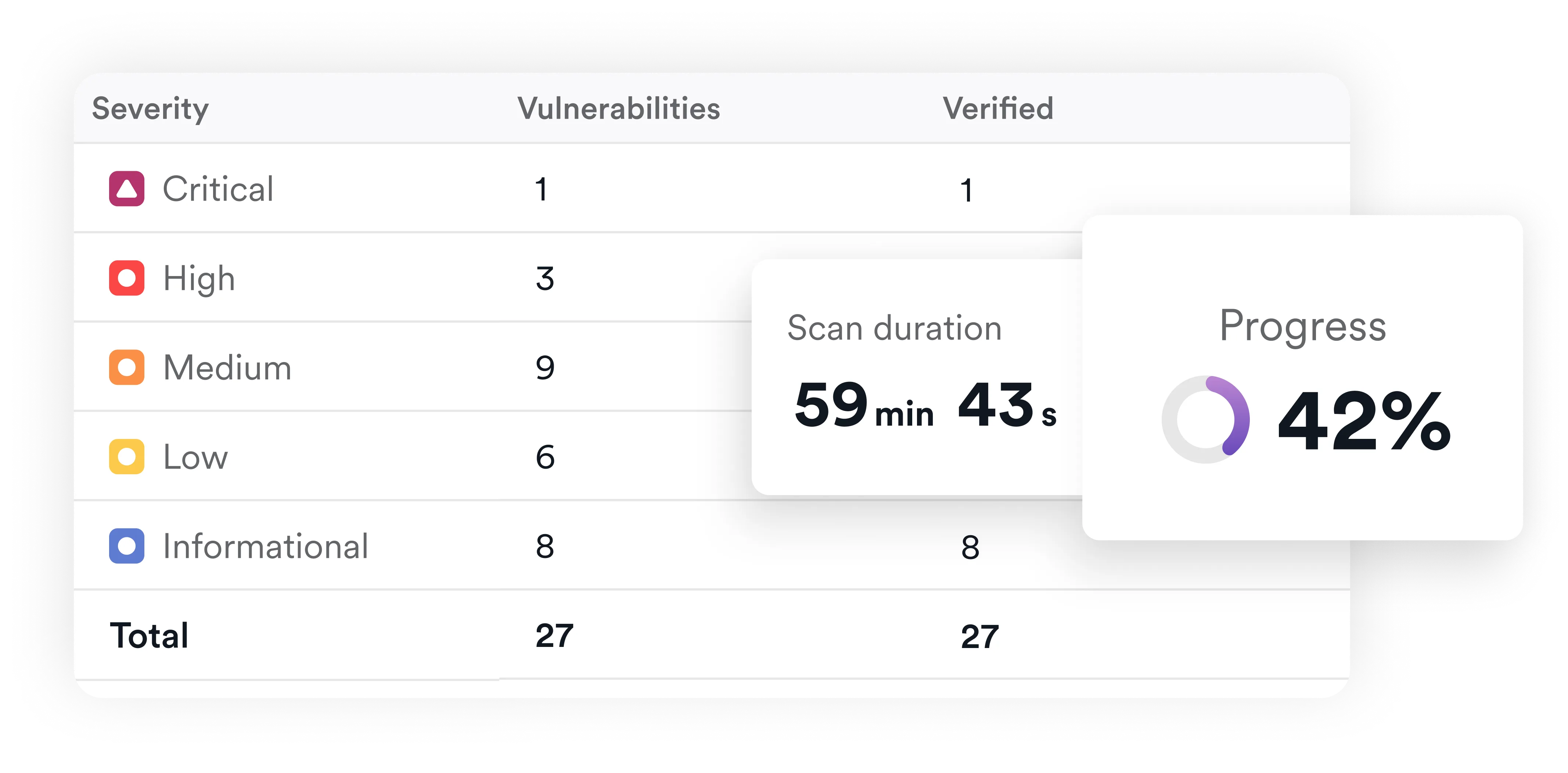
Many security tools flood teams with hypothetical issues. DAST cuts through that noise. Invicti’s proof-based scanning confirms exploitability, providing actionable evidence of real database vulnerabilities—no guesswork required. This lets you focus on prioritization and remediation, not triage.
Why Invicti’s DAST-first platform leads the field:
- Brings together DAST, SAST, IAST, API security, container security, and static and dynamic SCA for a centralized view
- Proof-based scanning verifies each vulnerability with real-world exploit simulations to fact-check security test findings
- Reduces alert fatigue by eliminating unconfirmed security vulnerabilities
- Integrates seamlessly into CI/CD pipelines and developer workflows for automated testing and remediation
- Helps teams audit and secure third-party plugins and dependencies
3600+ Top Organizations Trust Invicti
Secure your MySQL stack with proof, not noise. Feel the DAST-first difference.























