Netsparker Survey Results | Web Developers on Web Application Security, Governments, Most Vulnerable Industries & More
The results of the survey conducted by Netsparker. In this survey we asked developers questions about their test setup, web application security and more.

A few weeks ago one of our security researchers was experimenting with DNS Rebinding exploitation. By using such attack method he managed to attack vulnerable web applications hosted behind a firewall, practically bypassing a network firewall.
It is a very interesting attack and you can read Vulnerable Web Applications on Developers Computers Allow Hackers to Bypass Corporate Firewalls to learn more about this subject. Our researcher Sven also gave a live demo of how to bypass firewalls by exploiting vulnerabilities in web applications.
This attack method got us thinking about how many businesses are vulnerable to this type of attack. I mean every developer and security researcher have a half developed or vulnerable web application running in their test environment. With that in mind, and with all the hacking and election hacking news out there, we thought of doing a survey and ask developers some question which hopefully will give us a better insight of how vulnerable corporations are, and who is the biggest target.
Web Developers Demographics
Before diving into the interesting numbers, let's start with some demographics on the web developers who took the survey.
Age of Web Developers

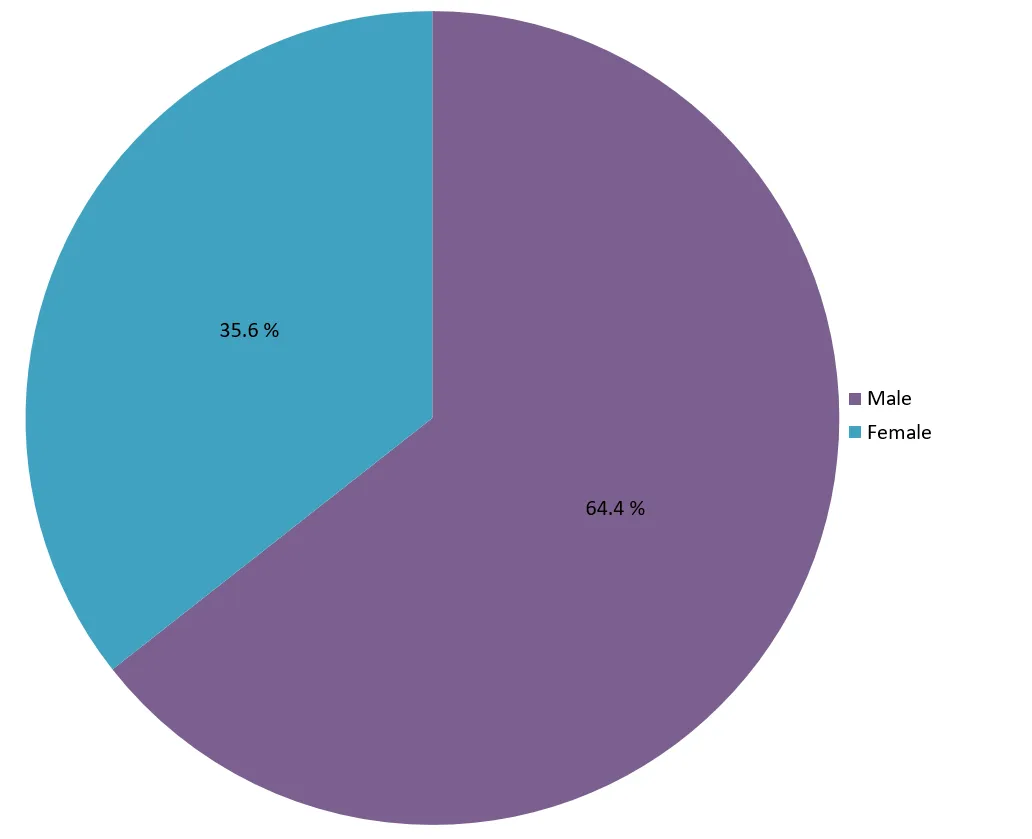
Gender of Web Developers
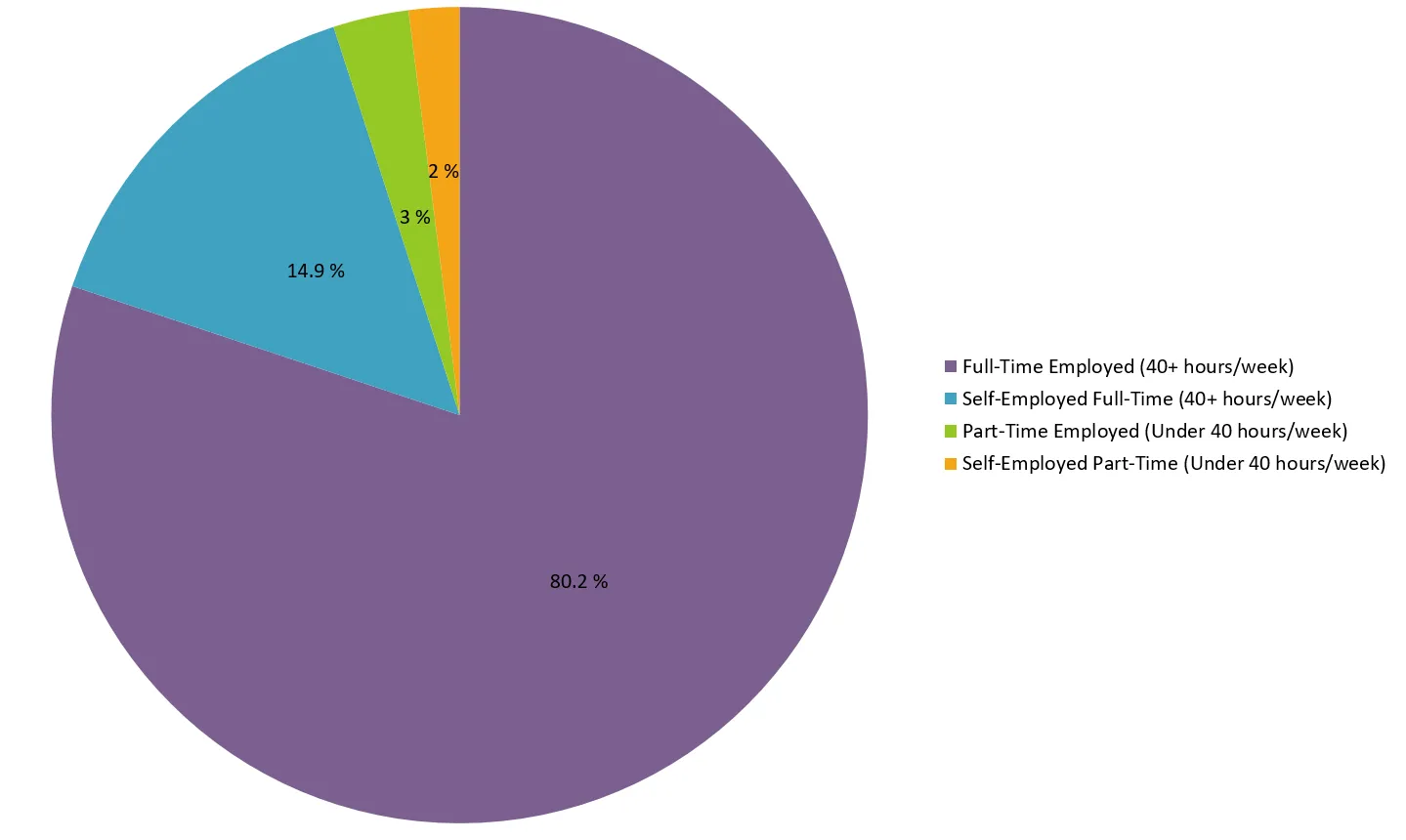
Employment status of Web Developers
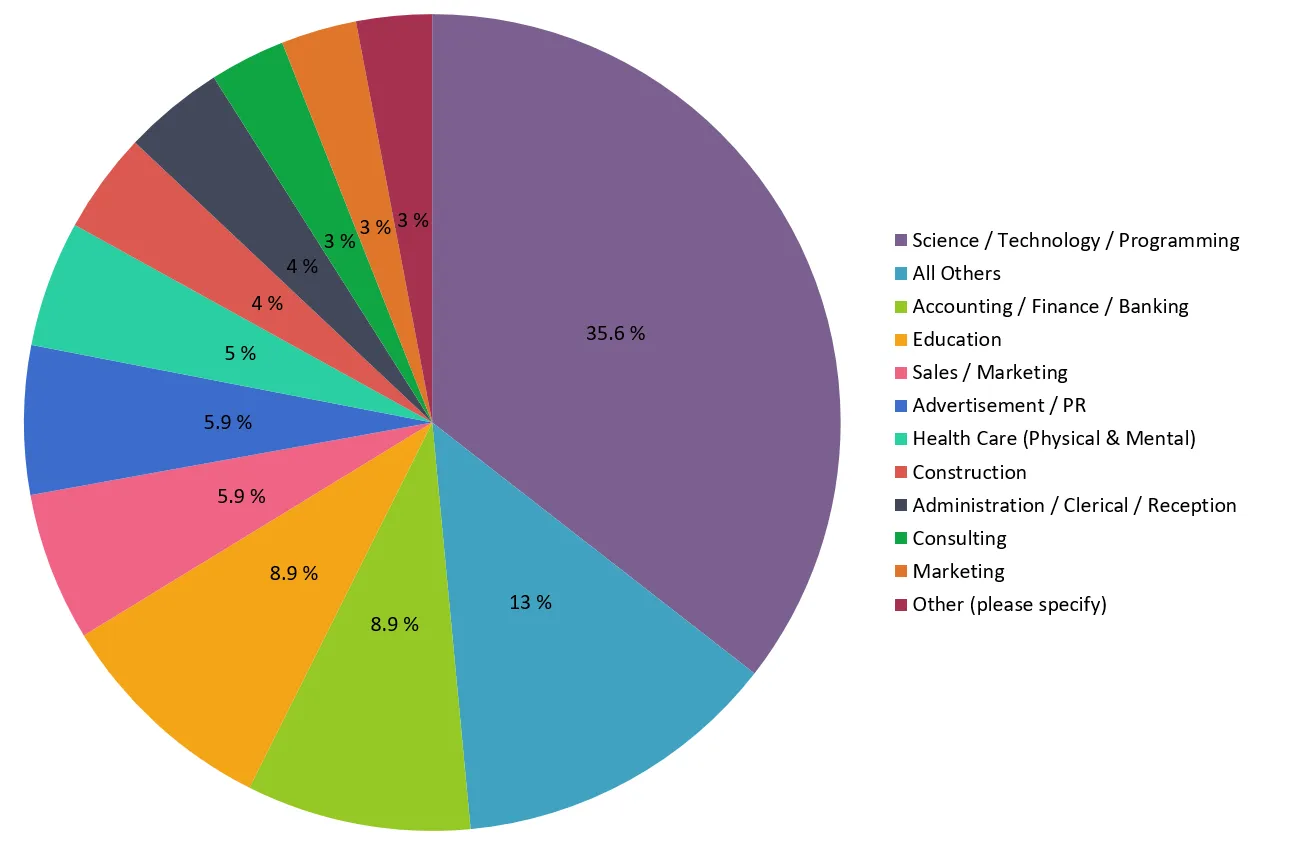
Industry Sector the Web Developers Work in
Web Developers Survey Questions
This is where the interesting stuff starts. Let's start with the obvious question:
Do you run a web server (LAMPP / XAMPP / IIS etc.) on your computer or test environment?

This is somehow surprising to me. To be honest I expected that 99% or all developers have some sort of web server configuration running on their computer or test environment.
Would you say that you typically keep your web server up-to-date?

It is good to see that 89.1% of the web developers we surveyed keep their web server software up to date. This is not surprising because we have really improved when it comes to patch management and network security.
Which of the following, if any, would you say are true of your test environment? (Select all that apply.)

Now, this is where it really starts becoming interesting, or even scary. More than half of the web developers who took the survey admit that sometimes they run half-developed and possibly vulnerable web applications on their computers. This is not bad and kind of expected. What is really scary is that 55.4% of them have connected such computers directly to the internet. That makes them a perfect easy target, even for a script kiddie!
The above also means that on average, one in two businesses are vulnerable to the attacks we mentioned earlier on, therefore should attackers do some homework and target them, they can bypass the victim's corporate firewalls and strike gold.
Which of the following vulnerabilities, if any, put democratic governments most at risk of an election hacking? (Select all that apply.)

So much has been said about the possibility of tampering with elections etc, but not much has been said on what could possibly allow the intruders to tamper with the process. The majority of the web developers we surveyed think that the top three problems are lack of IT expertise, outdated and possibly insecure polling equipment and that politicians do not believe this is a problem. The latter is true and it is frustrating when you see politicians living in their own cocoon denying such things.
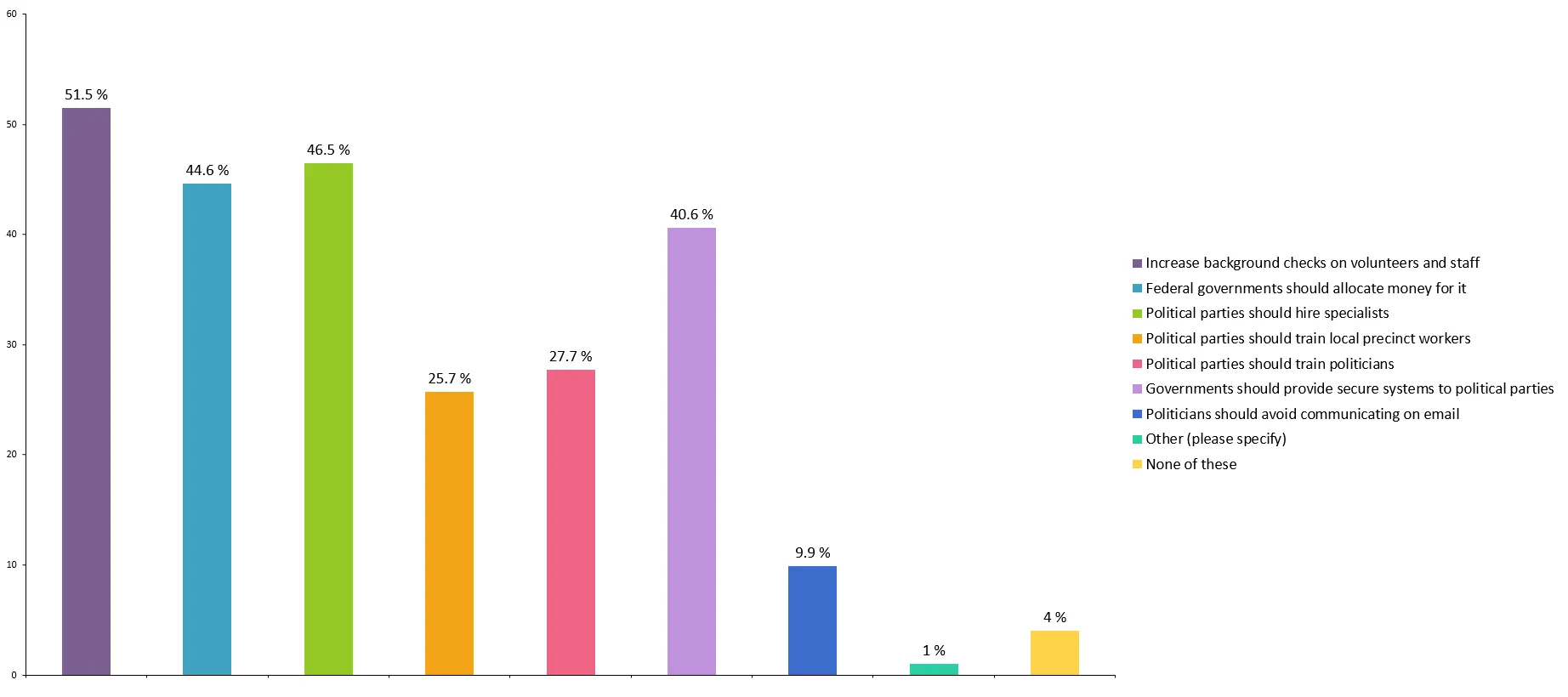
Which of the following preparations, if any, should democratic governments undergo in order to secure themselves against an election hacking? (Select all that apply.)
Which of the following concerns, if any, do you think prevent corporate boardrooms from taking cybersecurity seriously? (Select all that apply.)

It is very interesting to see that 57.4% of the web developers said that their management does not really understand IT. This clearly shows that even though one might have good managerial skills, it does not necessarily mean he is good at managing IT operations and departments. From my own personal experience, nothing beats hands on experience and there is no better manager than one who has worked in the field himself.
Which of the following actions, if any, should companies take in the event of a data breach? (Select all that apply.)
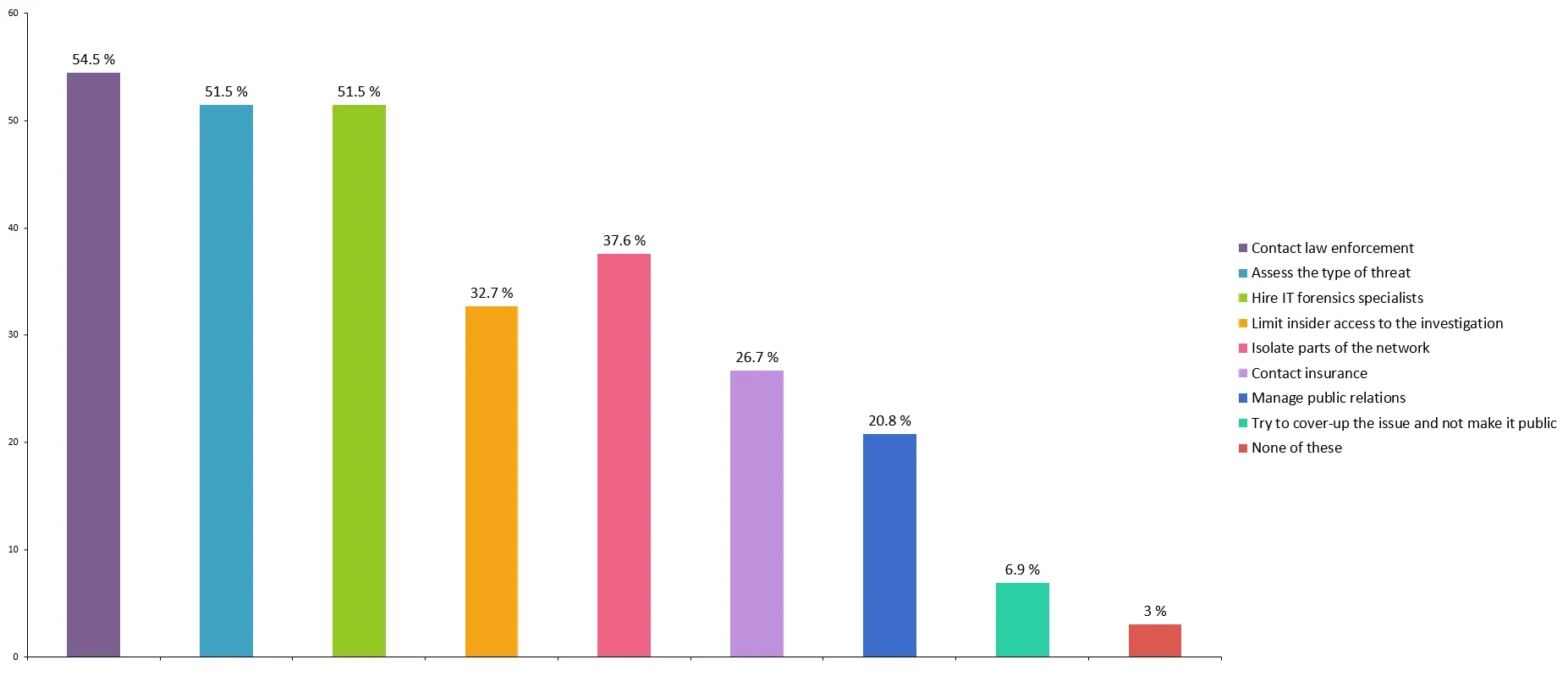
It might be a small percentage, but it is quite worrying that 6.9% of the developers who participated in the survey believe that companies should try to cover up hack attacks.
Which of the following industries, if any, do you think are most vulnerable to hacking? (Select all that apply.)

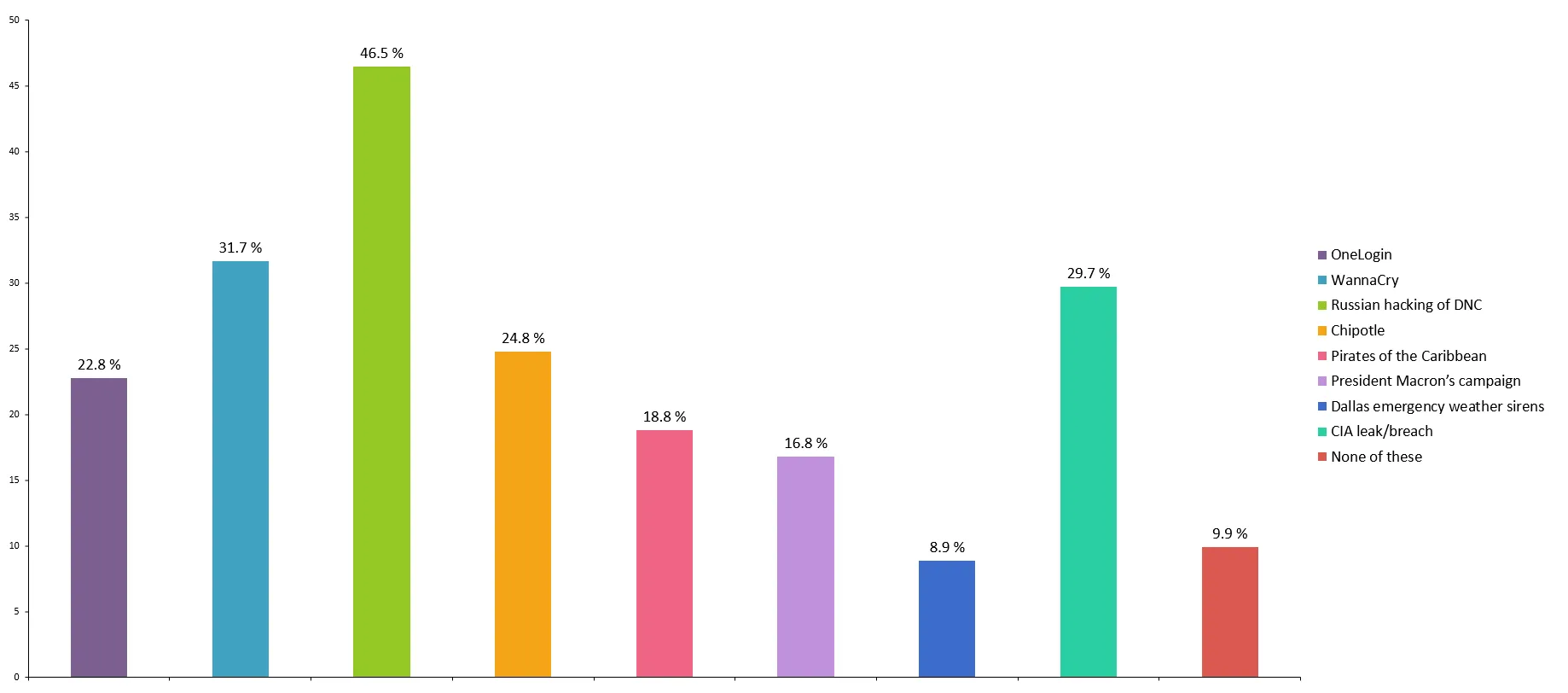
Which of the following recent hacks, if any, do you think has been the most innovative? (Select all that apply.)
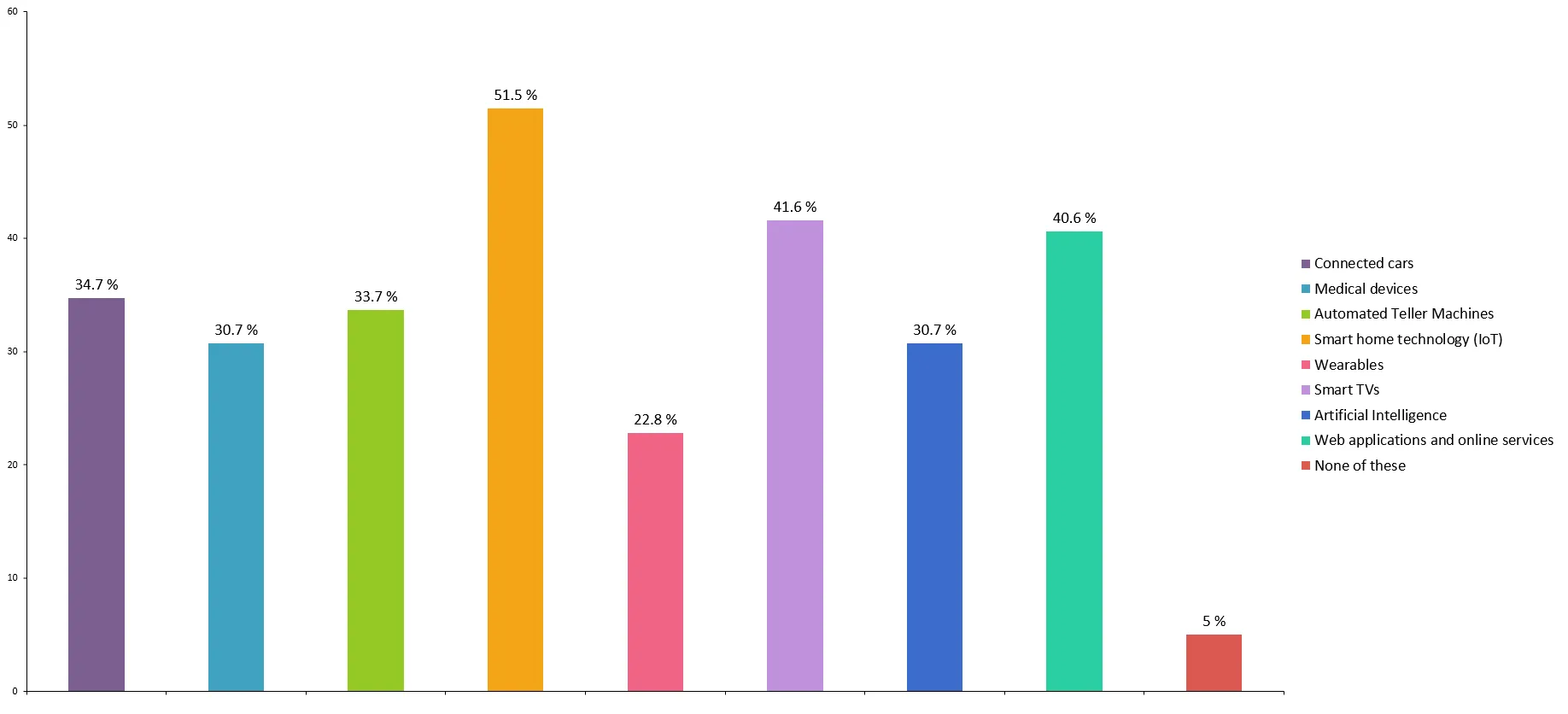
Which of the following technologies, if any, do you think are most at risk of future hacking for the rest of 2017? (Select all that apply.)
What Have We Learned from this Survey?
We kind of expected such results, but as always, there is a lot to take away from this survey. Here is a recap of what we’ve learnt:
- More than half of web developers run some sort of incomplete and possibly vulnerable web application. That means that more than half the businesses are possibly vulnerable to some sort of attack.
- Governments and political parties are the biggest target (political reasons / hacktivism etc) and they need to step up their game when it comes to cybersecurity.
- People in management should definitely get more involved and better inform themselves.
- Always contact law enforcement and assess the type of threat, if need be hire specialised IT forensics in case your business is hacked. Never try to cover up. If you try to do it to save the business’ reputation it might and most probably will backfire.
- After governments, web developers think (and they are right) that the most targeted industries are financial services, media, healthcare and manufacturing.
- Smart home technology (IoT), web applications & services, and connected cars will be the most targeted in the future.


